 |
 |
 |
| The CIsco Ironport Web Data Security solution |
|
|
 |
Data-stealing malware presents a real and imminent threat to business today,
and is the starting point for any discussion
on data security for the web. The Cisco IronPort web security appliance provides
the best protection against data-stealing
malware, using Cisco IronPort Web Reputation Filters, the Cisco IronPort Dynamic Vectoring and Streaming (DVS) engine
and the Layer 4 Traffc Monitor (L4TM). These technologies prevent Trojans and other malicious applications from entering the
network, while blocking the “phone home” data connections from existing malware.
The data loss problem extends well beyond malware. Employees can easily use webmail to
send a message including
proprietary information, post confdential data on social networks and blogs, or transfer fnancial documents over FTP to a
server outside the corporate network. Making sure that sensitive data does not leave
the corporate boundary – while allowing
users to leverage the full power of the Internet – is an important and challenging issue to solve.
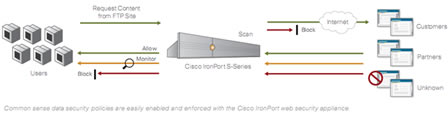
Cisco IronPort web security appliances enable organizations to take quick, easy steps to enforce simple, common sense data
security policies. For example, preventing engineers from sending design fles by webmail,
blocking uploads by fnance staff
of Excel spreadsheets over 100KB, or preventing posts of content to blogs or social networking sites. These simple data security policies can be created for outbound traffc on HTTP, HTTPS and FTP.
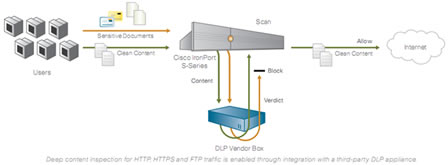
For enterprises that have already invested in special-purpose DLP systems, Cisco IronPort web security appliances offer the
option to interoperate with DLP vendors via ICAP. By directing all outbound HTTP, HTTPS and FTP traffc to the third-party
DLP appliance, organizations can allow or block based on the third-party rules and policies.
This also enables deep content
|
 |
 |
 |
inspection for regulatory compliance and intellectual property (IP) protection, incident severity defnition, case management and performance optimization.
|
 |
|
 |
|
 |



























