What is a Web Application Firewall (WAF)?
A web application firewall (WAF) safeguards web applications by filtering and monitoring HTTP traffic between the application and the internet. It commonly defends against attacks like cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection, among others.
A WAF operates as a protocol layer 7 defense in the OSI model and is not intended to counter every type of attack. This attack mitigation strategy is typically one component of a comprehensive suite of tools that collectively provide a robust defense against various attack vectors.
Deploying a WAF in front of a web application creates a shield between the application and the internet. Unlike a proxy server, which protects a client's identity by acting as an intermediary, a WAF functions as a reverse proxy. It protects the server from exposure by ensuring that all client requests pass through the WAF before reaching the server.
A WAF operates using a set of rules, commonly referred to as policies, designed to filter out malicious traffic and protect against application vulnerabilities. One key advantage of a WAF is the ability to swiftly modify these policies, enabling a rapid response to different attack vectors. For instance, during a DDoS attack, rate limiting can be quickly implemented by adjusting WAF policies.
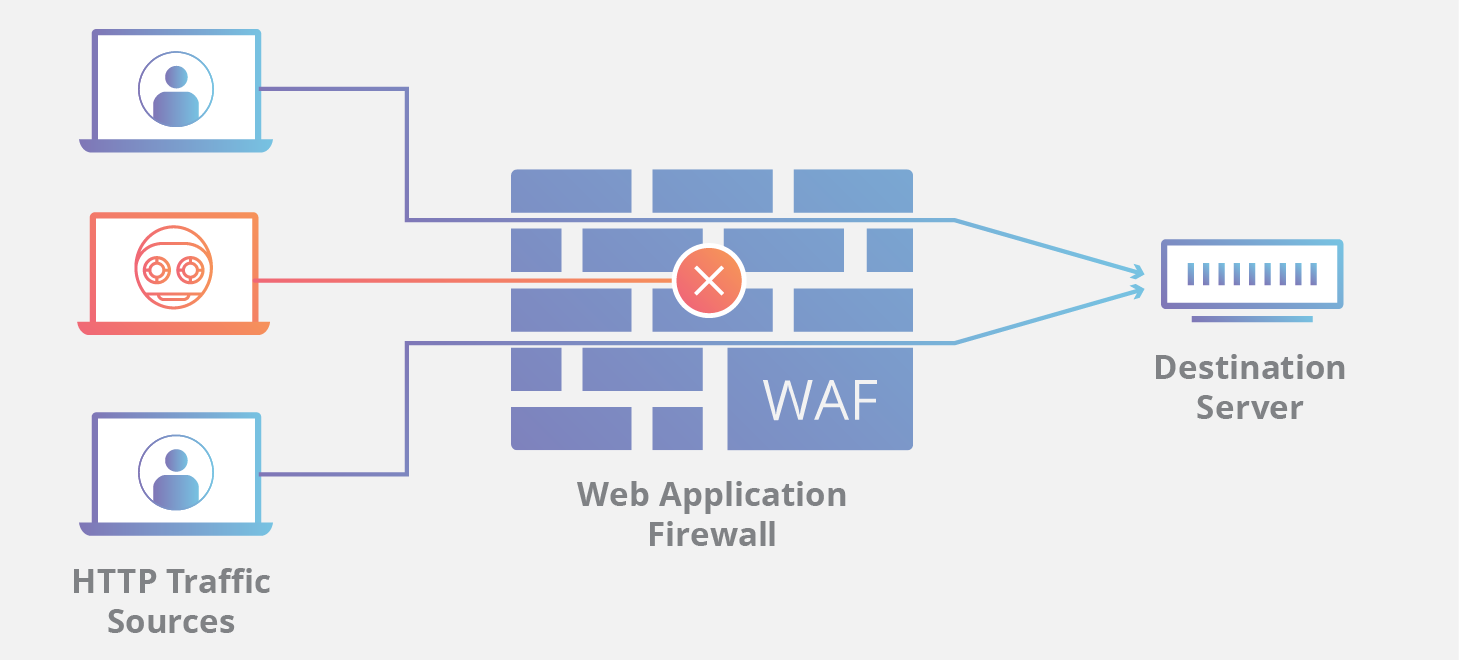
What is the difference between blocklist and allowlist WAFs?
A WAF that operates based on a blocklist (negative security model) protects against known attacks. It can be likened to a club bouncer who denies entry to guests who don’t meet the dress code. Conversely, a WAF based on an allowlist (positive security model) only admits traffic that has been pre-approved, similar to a bouncer at an exclusive party who only admits people on the guest list. Both blocklists and allowlists have their advantages and drawbacks, which is why many WAFs use a hybrid security model, implementing both approaches for enhanced protection.
What are network-based, host-based, and cloud-based WAFs?
A WAF can be implemented in one of three different ways, each with its own benefits and shortcomings:
- Network-based WAFs : These are typically hardware appliances installed within the network. They offer high performance and low latency since they are deployed close to the web servers. However, they can be expensive and complex to maintain.
- Host-based WAFs : These are software solutions installed directly on the web server. They are highly customizable and can be integrated with other host-based security tools. However, they can consume significant server resources and may require more maintenance and updates.
- Cloud-based WAFs : These are managed services provided by third-party vendors. They are easy to deploy and scale, with minimal upfront costs. However, they can introduce additional latency due to traffic routing and may depend on the reliability of the third-party provider.
- HTTP Headers : These contain metadata about the request or response, such as the source and destination addresses, cookies, and content types. Malicious actors often manipulate headers to execute attacks.
- HTTP Body : This is the main content of the request or response, which can include user input, form submissions, and data exchange. The body is scrutinized for malicious payloads like SQL injection or cross-site scripting (XSS) attempts.
- URL Parameters : These are key-value pairs added to the URL to pass data between the client and the server. Attackers may exploit these parameters to inject malicious code.
- Cookies : These are small pieces of data stored on the client side and sent with each request to the server. WAFs examine cookies for signs of tampering or malicious intent.
- Block Malicious Traffic: WAFs prevent data breaches and other attacks by blocking malicious traffic before it reaches a web application.
- Protect Sensitive Data: WAFs safeguard sensitive information, such as credit card numbers and Personally Identifiable Information (PII), from unauthorized access.
- Compliance: WAFs help meet compliance requirements, such as PCI DSS, by blocking traffic that violates these standards.
- Layered Defense: WAFs can work alongside other security tools, like intrusion detection systems (IDS), intrusion prevention systems (IPS), and firewalls, to create a more effective layered defense against attacks.
Each method offers distinct advantages and limitations, and the choice of implementation depends on the specific needs and resources of the organization.
How does a WAF work?
A WAF works by inspecting HTTP requests and applying predefined rules to identify malicious traffic. It can be implemented as software, an appliance, or a service. The WAF analyzes the following key parts of HTTP conversations:
By analyzing these components, a WAF can effectively detect and block various types of web attacks.
Why is WAF security important?
WAFs are crucial for the security of online businesses. They protect sensitive data, prevent leaks, block malicious code from being injected into servers, and help meet compliance requirements like the Payment Card Industry Data Security Standard (PCI DSS). As organizations increasingly use more web applications and IoT devices, attackers target their vulnerabilities. Integrating a WAF with other security tools, such as two-factor authentication (2FA) and malware protection, creates a robust defense strategy.
What is the difference between WAF and other tools?
While network firewalls handle lower layers, WAFs focus on higher layers where web applications are more vulnerable. WAFs are vital for robust application security.
How does WAF contribute to web app security?
Many applications today are created using a combination of home-grown, third-party, and open-source code. WAFs add an extra layer of security to inadequately built or legacy applications and help enhance secure design practices by blocking common attack vectors and preventing malicious traffic from reaching the application. Below are significant advantages specific to WAFs:
Find the right solution for your business with Ruth Victor
And more enterprise-grade solutions to protect your digital assets.
